Maximizing SIEM Efficiency: A Guide to Prioritizing Log Sources for Effective SOC Implementation
Security information and event management (SIEM) is an essential part of a strong cybersecurity strategy. It helps organizations detect and respond to security incidents by collecting and analyzing logs from a variety of sources. To deploy SIEM effectively, it’s important to prioritize log sources for maximum efficiency. This guide explores the importance of log sources in SIEM and provides best practices for prioritizing them to improve your Security Operations Center (SOC) implementation.
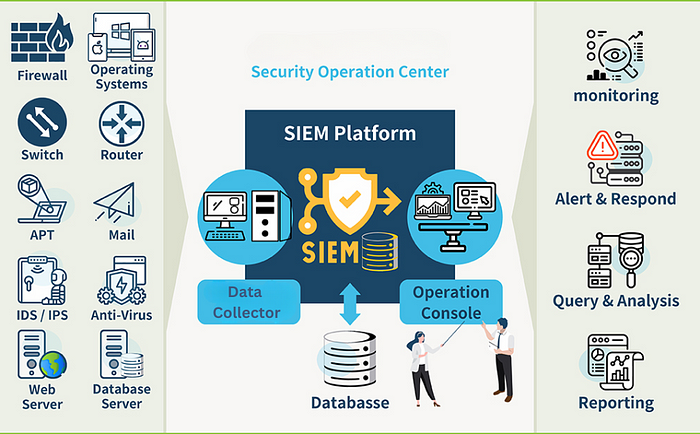
Understanding the Importance of Log Sources in SIEM
Log sources form the foundation of SIEM, providing valuable information about network activities, system events, and user behavior. They include many types of data, including firewall logs, intrusion detection system logs, authentication logs, and more. By aggregating and correlating these logs, SIEM solutions can identify potential threats and security incidents in real-time.
To maximize SIEM effectiveness, it is essential to understand the importance of each log source. Some log sources may contain important information that can help detect advanced threats, while others may provide information about insider threats or compliance violations. By prioritizing log sources based on their relevance and potential impact, organizations can allocate resources effectively and focus on the most important security risks.
Key Considerations for Prioritizing Log Sources
When prioritizing log sources for SIEM, there are some key considerations to keep in mind:
1. Relevance to Security Objectives:
Evaluate the relevance of each log source to your organization’s security goals. Focus on log sources that provide information about potential threats or vulnerabilities that align with your security goals. For example, if your organization is highly concerned about unauthorized access attempts, prioritizing authentication logs is important.
2. Regulatory and Compliance Requirements:
Consider legal and compliance requirements specific to your industry. Log sources that help meet these requirements should be given high priority. For example, healthcare organizations can prioritize logs related to the access and handling of sensitive patient information to comply with HIPAA regulations.
3. Potential Impact and Severity:
Assess the potential impact and severity of security incidents that may be detected through specific log sources. Log sources with a higher probability of detecting important security events should be prioritized accordingly. This ensures that your SOC team can focus on addressing the most important threats first.
Identifying Critical Log Sources for Effective SOC Implementation
To effectively implement SIEM and SOC monitoring, it is crucial to identify critical log sources. Here are some log sources that are typically considered essential for a comprehensive SOC implementation:
1. Firewall Logs:
Firewalls play a vital role in securing network perimeters. Analyzing firewall logs can help detect unauthorized access attempts, port scans, and other suspicious activities. Prioritize firewall logs to ensure prompt detection and response to potential network breaches.
2. Intrusion Detection System (IDS) Logs:
IDS logs provide insights into potential intrusion attempts and unauthorized activities within your network. By analyzing IDS logs, SOC teams can identify patterns and indicators of compromise, enabling them to take proactive measures to mitigate threats.
3. Endpoint Logs:
Endpoint logs, including those from workstations and servers, provide visibility into user activities and potential security incidents at the device level. Monitoring these logs can help identify malware infections, suspicious file activity, and other indicators of compromise.
4. Application Logs:
Application logs contain valuable information about application activities and can help detect anomalies, such as unauthorized access attempts or suspicious transactions. Prioritize application logs based on the criticality of the applications and the potential impact of security incidents.
5. Authentication Logs:
Authentication logs provide insights into user login activities, failed login attempts, and potential brute force attacks. By analyzing authentication logs, SOC teams can detect unauthorized access attempts and take appropriate actions to prevent further compromise.
By focusing on these critical log sources, organizations can lay a strong foundation for an effective SOC implementation and enhance their ability to detect and respond to security incidents promptly.
Best Practices for Logging and Monitoring in SIEM
To maximize SIEM efficiency, it is essential to follow best practices for logging and monitoring. Here are some key recommendations:
1. Define Clear Logging Policies:
Establish clear logging policies that outline what events should be logged, including log sources, log levels, and retention periods. Ensure that these policies align with your organization’s security objectives and compliance requirements.
2. Enable Centralized Log Management:
Implement a centralized log management system that aggregates logs from various sources. This allows for efficient log collection, storage, and analysis. Consider leveraging SIEM solutions that offer robust log management capabilities.
3. Regularly Review and Update Log Sources:
Periodically review and update your log sources to adapt to evolving security threats and organizational changes. New applications, network devices, or cloud services may require additional log sources to be integrated into your SIEM solution.
4. Implement Real-time Log Monitoring:
Enable real-time log monitoring to detect and respond to security incidents promptly. Leverage automated alerts and correlation rules to identify potential threats and anomalies in real time.
5. Conduct Regular Log Analysis and Reporting:
Regularly analyze logs to identify patterns, trends, and potential security incidents. Generate comprehensive reports to provide visibility into the security posture of your organization and support decision-making processes.
By following these best practices, organizations can ensure that their SIEM implementation is optimized for maximum efficiency and effectiveness.
Example of a Comprehensive SIEM Log Source Hierarchy
A comprehensive SIEM log source hierarchy helps organizations structure their log collection and analysis processes. Here is an example of a log source hierarchy that demonstrates the relationship between different log sources:
Network Logs:
- Firewall Logs
- Router Logs
- Switch Logs
System Logs:
- Operating System Logs
- Application Logs
- Database Logs
Security Logs:
- Intrusion Detection System (IDS) Logs
- Intrusion Prevention System (IPS) Logs
- Anti-malware Logs
User Activity Logs:
- Authentication Logs
- Privileged User Logs
- User Behavior Analytics (UBA) Logs
By organizing log sources into a hierarchy, organizations can better prioritize their collection and analysis efforts, ensuring that critical log sources receive the necessary attention.
Tools for Efficient Log Collection and Analysis
To maximize SIEM efficiency, organizations can leverage various tools for log collection and analysis. Here are some commonly used tools:
1. SIEM Solutions:
SIEM solutions provide the necessary infrastructure for log collection, storage, and analysis. They offer features such as real-time monitoring, correlation rules, and automated alerts, enabling efficient threat detection and response.
2. Log Management Systems:
Log management systems help centralize and manage logs from various sources. They provide scalable storage, search capabilities, and log retention policies, ensuring that organizations can efficiently analyze logs and meet compliance requirements.
3. Security Orchestration, Automation, and Response (SOAR) Platforms:
SOAR platforms automate security operations, including log collection, analysis, and incident response. They streamline workflows, enabling SOC teams to focus on critical tasks and improve overall efficiency.
4. Endpoint Detection and Response (EDR) Solutions:
EDR solutions provide enhanced visibility and threat detection capabilities at the endpoint level. They collect and analyze endpoint logs, enabling proactive threat hunting and incident response.
By leveraging these tools, organizations can streamline log collection and analysis processes, enabling efficient detection and response to security incidents.
Challenges and Solutions in Managing Log Sources
Managing log sources can present several challenges for organizations. Here are some common challenges and their corresponding solutions:
1. Volume of Logs:
The sheer volume of logs generated by various sources can overwhelm organizations, making it challenging to analyze and respond to security incidents promptly. Implementing log management systems with scalable storage and real-time analysis capabilities can help address this challenge.
2. Log Source Integration:
Integrating log sources from diverse systems, applications, and network devices can be complex. Organizations should leverage standardized log formats, such as Syslog or Common Event Format (CEF), and SIEM solutions with pre-built integrations to simplify the log source integration process.
3. Log Source Visibility:
Lack of visibility into certain log sources can hinder the effectiveness of SIEM and SOC monitoring. Regularly review and update log sources to ensure comprehensive coverage and visibility into potential security incidents.
4. Log Source Validation:
Validating log sources and ensuring the accuracy and integrity of log data is crucial. Implement log validation mechanisms, such as secure log transport protocols and digital signatures, to prevent tampering or unauthorized modifications.
By addressing these challenges proactively, organizations can optimize log source management and enhance the effectiveness of their SIEM and SOC implementation.
Implementing a Log Management Strategy for Maximum SIEM Efficiency
To maximize SIEM efficiency, organizations should implement a log management strategy that addresses key aspects of log collection, analysis, and storage. Here are some essential steps to consider:
1. Define Log Collection Requirements:
Identify and document the log collection requirements based on your organization’s security objectives, compliance requirements, and industry best practices. Consider the log sources that need to be collected, log levels, and retention periods.
2. Establish Log Source Prioritization:
Prioritize log sources based on their relevance to security objectives, potential impact, and compliance requirements. Assign appropriate resources and allocate sufficient storage capacity to critical log sources.
3. Implement Log Collection Mechanisms:
Implement log collection mechanisms, such as agents, forwarders, or log collectors, to efficiently collect logs from various sources. Ensure that these mechanisms are properly configured, secure, and capable of handling the volume and velocity of log data.
4. Establish Log Analysis and Retention Processes:
Implement log analysis processes, including automated log parsing, correlation rules, and real-time monitoring. Define log retention periods based on compliance requirements and establish processes for secure log storage and archiving.
5. Regularly Monitor and Review Log Sources:
Continuously monitor and review log sources to ensure their effectiveness in detecting security incidents. Conduct regular audits and assessments to identify gaps or areas for improvement in your log management strategy.
By implementing a well-defined log management strategy, organizations can enhance SIEM efficiency, improve threat detection capabilities, and strengthen their overall cybersecurity posture.
Log sources play a crucial role in a successful SOC implementation. By prioritizing log sources based on their relevance, potential impact, and compliance requirements, organizations can maximize SIEM efficiency and improve their ability to detect and respond to security incidents promptly.
Implementing best practices for logging and monitoring, using a comprehensive log source hierarchy, and leveraging efficient log collection and analysis tools are essential steps for optimizing SIEM effectiveness. Overcoming challenges in managing log sources and implementing a robust log management strategy further enhances SIEM efficiency and strengthens an organization’s cybersecurity defenses.
By recognizing the importance of log sources and implementing a prioritization strategy, organizations can enhance their SOC monitoring capabilities and stay one step ahead of evolving cyber threats.
